Footprinting Lab - Medium
Important notes⌗
- Target IP -> 10.129.152.229
- Found credentials -> alex:lol123!mD
First, we use nmap -sC -sV <ip> to scan the services on the target.
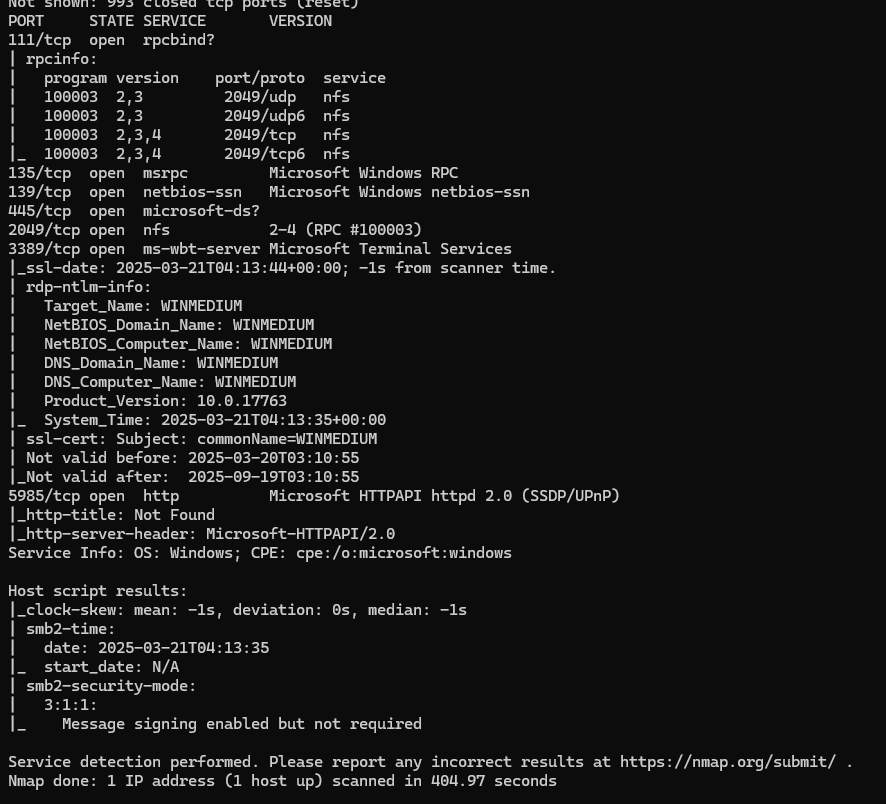
We can see we have RPC, NFS and SMB ports. Let’s start with NFS.
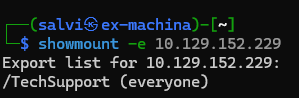
Ok. We have a TechSupport directory. Let’s mount it to our system.
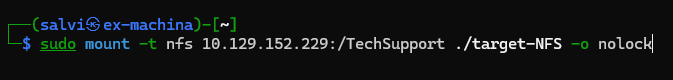
We need root permission to access the directory. Let’s change to root and access it.
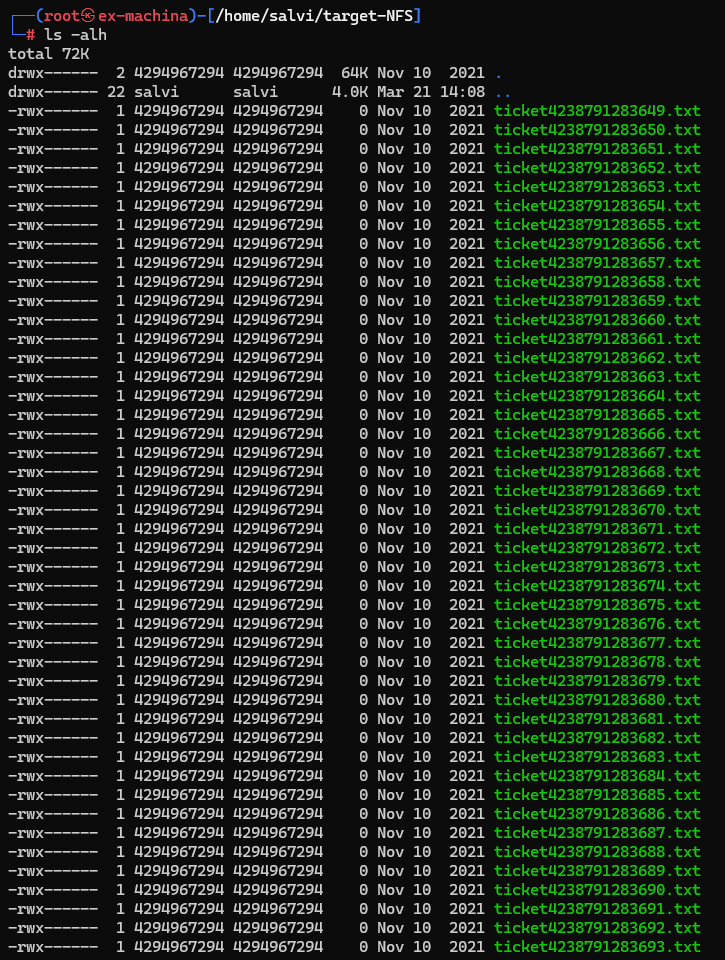
We have a lot of tickets here. But one brings out our attention more then others.
Ticket number 4238791283782, is 1.3K in size. Let’s see what’s inside.
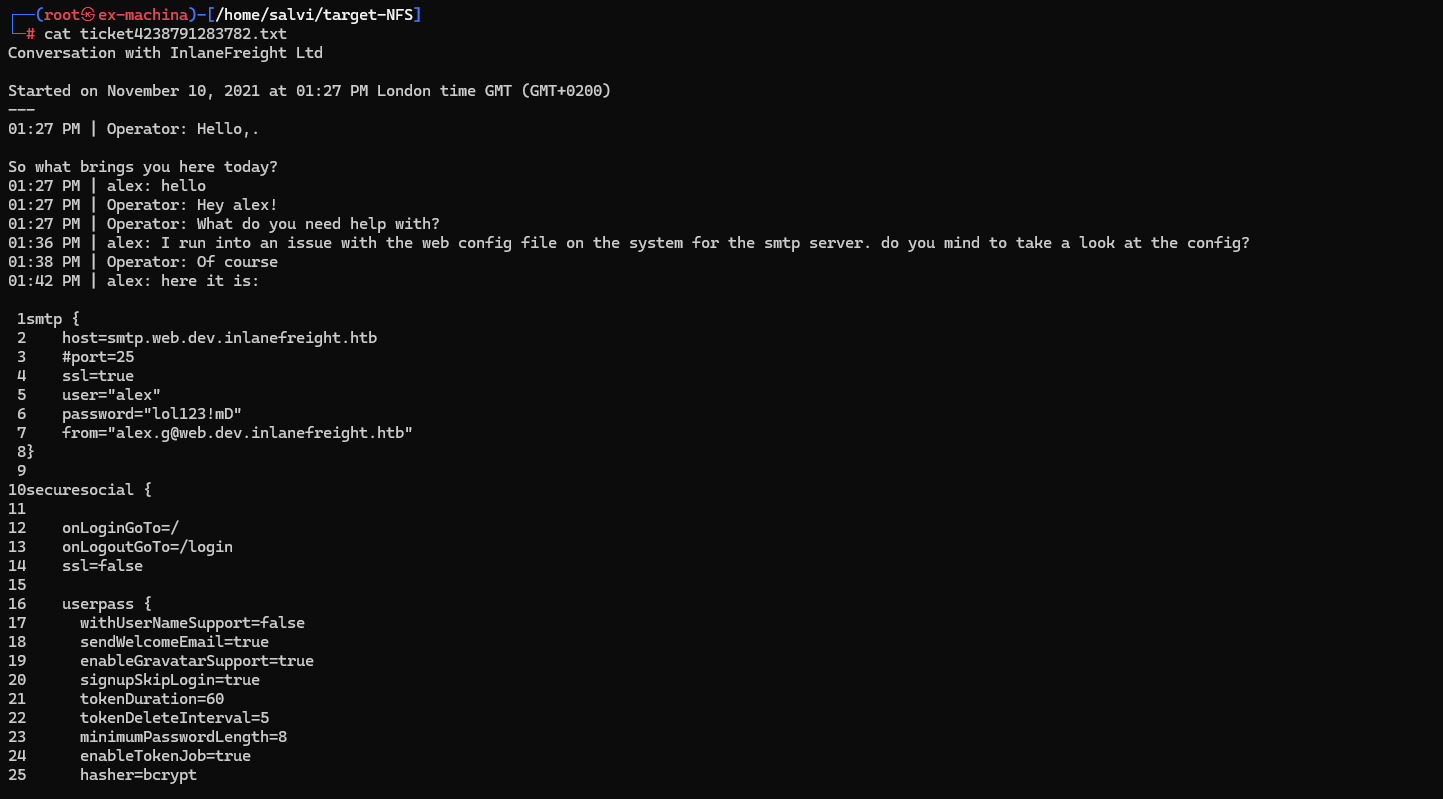
A user and a password a SMTP service. Great! Let’s try it on the SMB.
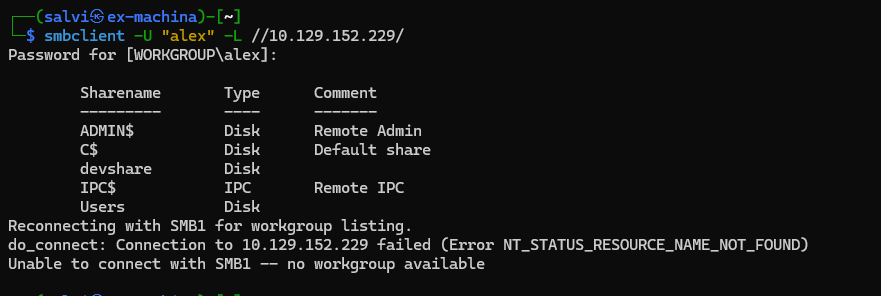
Ok. We have enumerated the sharenames of the SMB. So the login worked. Let’s access devshare first.
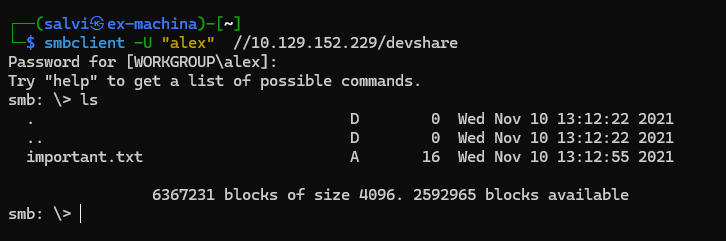
Let’s see what’s so important.
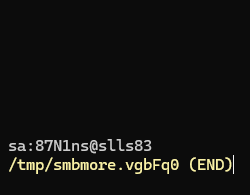
Looks like some credentials. Could be the system admin for the RPC.
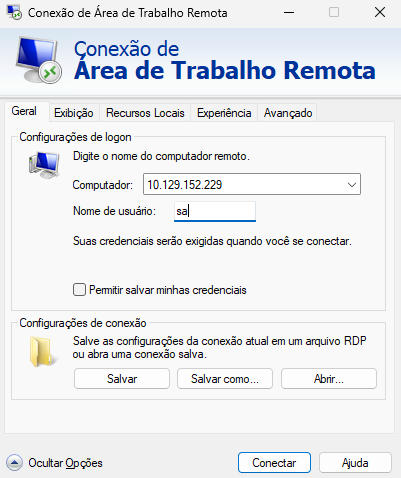
Didn’t work.
![[{E3E13AC1-9DD1-46F1-9DD2-16C169F2BD04} 1.png]]
Let’s try alex.
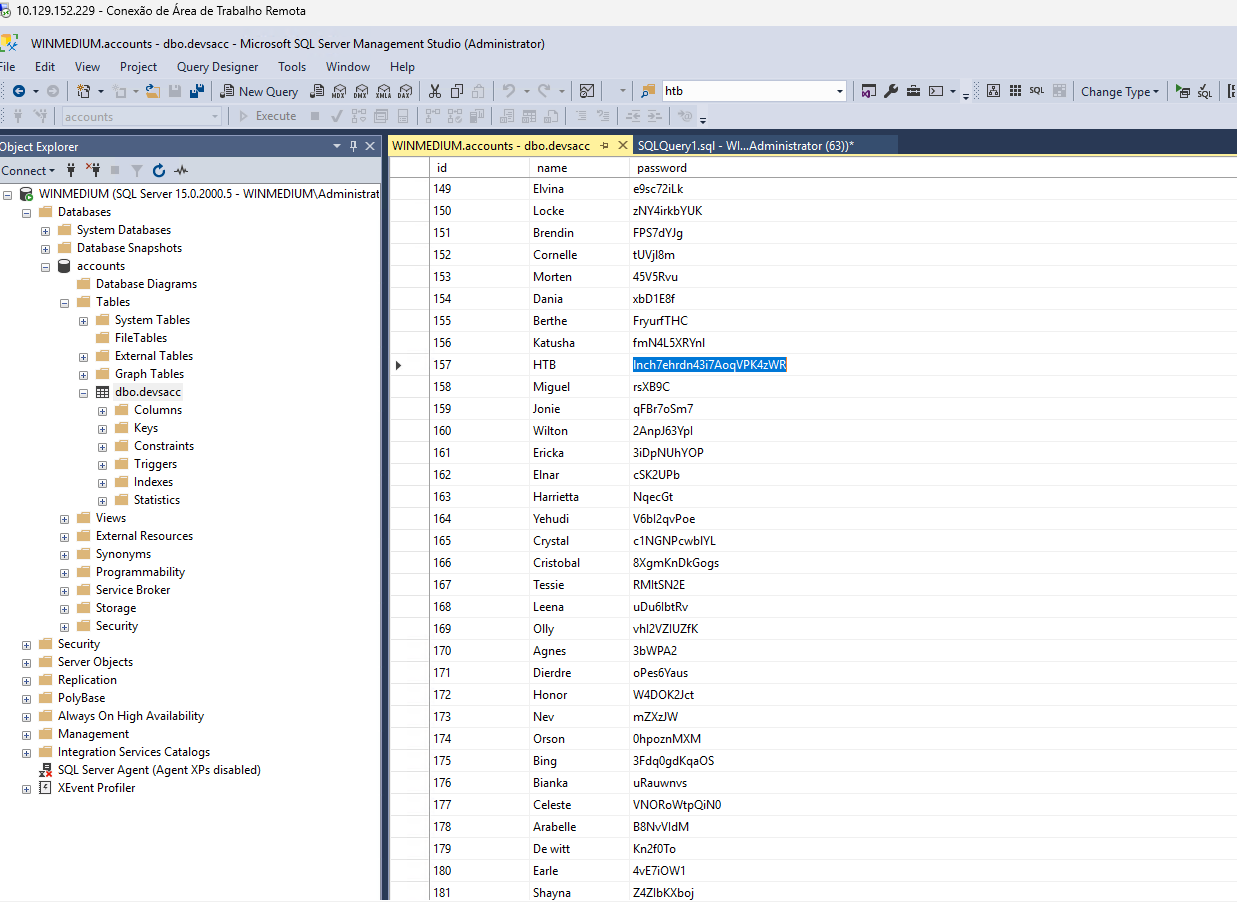
We are in! Now let’s find the HTB user and grab that flag.
Run the MSSQLManager as an admin.
Now we can use the credentials found at important.txt.
Editing the firs 200 rows form accounts, we find the flag.